Web servers and the application code running on those as a simple website or web portal, are vulnerable to various attacks. In one type of attack, the hacker can simply deface the pages, while in other serious types, the attacker can potentially steal data and disrupt website operations. It is important to understand that merely having firewalls is not enough, hence a detailed Web Application VAPT on regular intervals of time is recommended.
Web Application VAPT
We perform Automated Vulnerability Scanning as well as exhaustive manual pen testing to identify flaws in your web application security and business logic related vulnerabilities.
Benefits of our Web Application VAPT Service
You get robust threat exploration of each web application you deploy. Identify security vulnerabilities, weakness, and technical flaws.
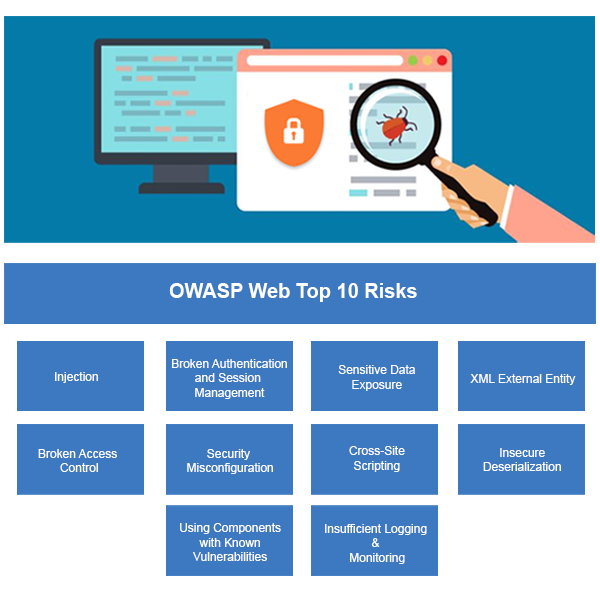
Our Web Application Vulnerability Assessment and Pen Tests consider the following factors:
- Command Injection (SQL Injection, Code Injection)
- Cross site scripting (XSS)
- Checking for backdoors
- Session Hijacking
- Buffer overflows
- Trust boundary violation
- Unhandled array declaration
- Unchecked return values
- OWASP Top 10